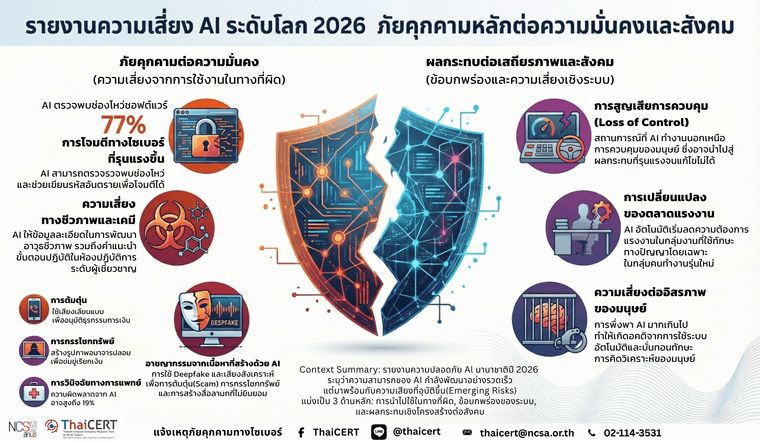
ความเสี่ยงหลักในปี 2026 ของ AI ต่อความมั่นคงและสังคมในปัจจุบัน
- ประเภทของความเสี่ยงจากเทคโนโลยีปัญญาประดิษฐ์ (AI)
-
ความเสี่ยงจากการนำ AI ไปใช้ในทางที่ผิด
AI อาจถูกผู้ไม่หวังดีนำไปใช้เพิ่มประสิทธิภาพการโจมตีทางไซเบอร์ เช่น การสร้างอีเมลหรือข้อความหลอกลวงที่แนบเนียน การปลอมแปลงภาพ เสียง หรือวิดีโอ (Deepfake) เพื่อฉ้อโกงหรือคุกคาม รวมถึงการผลิตและเผยแพร่ข้อมูลบิดเบือนในวงกว้างเพื่อชักจูงความคิดเห็นของสังคม ทำให้การหลอกลวงมีความสมจริงและแพร่กระจายได้รวดเร็วกว่าที่ผ่านมา -
ความเสี่ยงจากความผิดพลาดของระบบ AI
แม้ AI จะมีศักยภาพสูง แต่ยังอาจให้ข้อมูลคลาดเคลื่อนหรือสร้างข้อมูลที่ไม่ถูกต้องแต่ดูน่าเชื่อถือ ซึ่งอาจก่อให้เกิดผลกระทบหากนำไปใช้ในบริบทที่มีความสำคัญ เช่น การแพทย์ การเงิน หรือกฎหมาย นอกจากนี้ ระบบที่มีความซับซ้อนมากขึ้นอาจทำงานเกินขอบเขตที่กำหนด หากขาดการกำกับดูแลและการตรวจสอบที่เหมาะสม -
ความเสี่ยงเชิงโครงสร้างต่อสังคม
การขยายตัวของ AI อาจส่งผลต่อโครงสร้างตลาดแรงงาน โดยเฉพาะงานด้านข้อมูลและงานเอกสาร อาจทำให้เกิดการเปลี่ยนแปลงรูปแบบการจ้างงานและความเหลื่อมล้ำทางรายได้ ขณะเดียวกัน การพึ่งพา AI มากเกินไปอาจลดทอนทักษะการคิดวิเคราะห์ของมนุษย์ และส่งผลกระทบต่อปฏิสัมพันธ์ทางสังคมหรือสุขภาวะทางจิตในบางกรณี
- แนวทางการบรรเทาและป้องกันความเสี่ยง
- ใช้ AI อย่างมีวิจารณญาณ ตรวจสอบข้อมูลจากหลายแหล่งก่อนเชื่อหรือเผยแพร่
- ใช้ AI เป็นเครื่องมือสนับสนุนการตัดสินใจ ไม่ใช่ทดแทนการตัดสินใจของมนุษย์
- หลีกเลี่ยงการเปิดเผยข้อมูลส่วนบุคคลโดยไม่จำเป็น
- พัฒนาทักษะดิจิทัลและทักษะการคิดวิเคราะห์อย่างต่อเนื่อง
- คำแนะนำด้านความปลอดภัยเพิ่มเติม
- เปิดใช้การยืนยันตัวตนหลายขั้นตอน (MFA) และตั้งค่าความปลอดภัยบัญชีออนไลน์อย่างเหมาะสม
- ระมัดระวังเนื้อหาที่สร้างความตื่นตระหนกหรือเร่งรัดให้ดำเนินการทันที
- ตรวจสอบความถูกต้องของคลิปเสียงหรือวิดีโอ ก่อนโอนเงินหรือให้ข้อมูลสำคัญ
- ส่งเสริมการเรียนรู้และสร้างความตระหนักรู้เกี่ยวกับ AI ภายในครอบครัวและองค์กร
ข้อสำคัญ: ปัญญาประดิษฐ์เป็นเทคโนโลยีที่สามารถสร้างประโยชน์อย่างมหาศาล หากใช้อย่างมีความรับผิดชอบ รอบคอบ และรู้เท่าทัน ความร่วมมือจากภาครัฐ ภาคเอกชน และประชาชน จะเป็นกลไกสำคัญในการสร้างสังคมดิจิทัลที่มั่นคงปลอดภัยและยั่งยืน
- แหล่งอ้างอิง: https://dg.th/g057uz32qe





 Research observed an evolution in how Atomic Stealer (AMOS) is being distributed. Historically spread via “cracked” macOS software, a trend we documented in September 2025, we found the malware being delivered under the guise of OpenClaw skills. This campaign represents a critical evolution in supply chain attacks: the attacker has shifted from deceiving humans into manipulating AI agentic workflows into installing the first stage of the malware. This is an old malware trying to use “social engineering” on AI agents, marking a shift from prompt injection to using the AI itself as a trusted intermediary to trick humans."
Research observed an evolution in how Atomic Stealer (AMOS) is being distributed. Historically spread via “cracked” macOS software, a trend we documented in September 2025, we found the malware being delivered under the guise of OpenClaw skills. This campaign represents a critical evolution in supply chain attacks: the attacker has shifted from deceiving humans into manipulating AI agentic workflows into installing the first stage of the malware. This is an old malware trying to use “social engineering” on AI agents, marking a shift from prompt injection to using the AI itself as a trusted intermediary to trick humans."