Industrial Sector
-
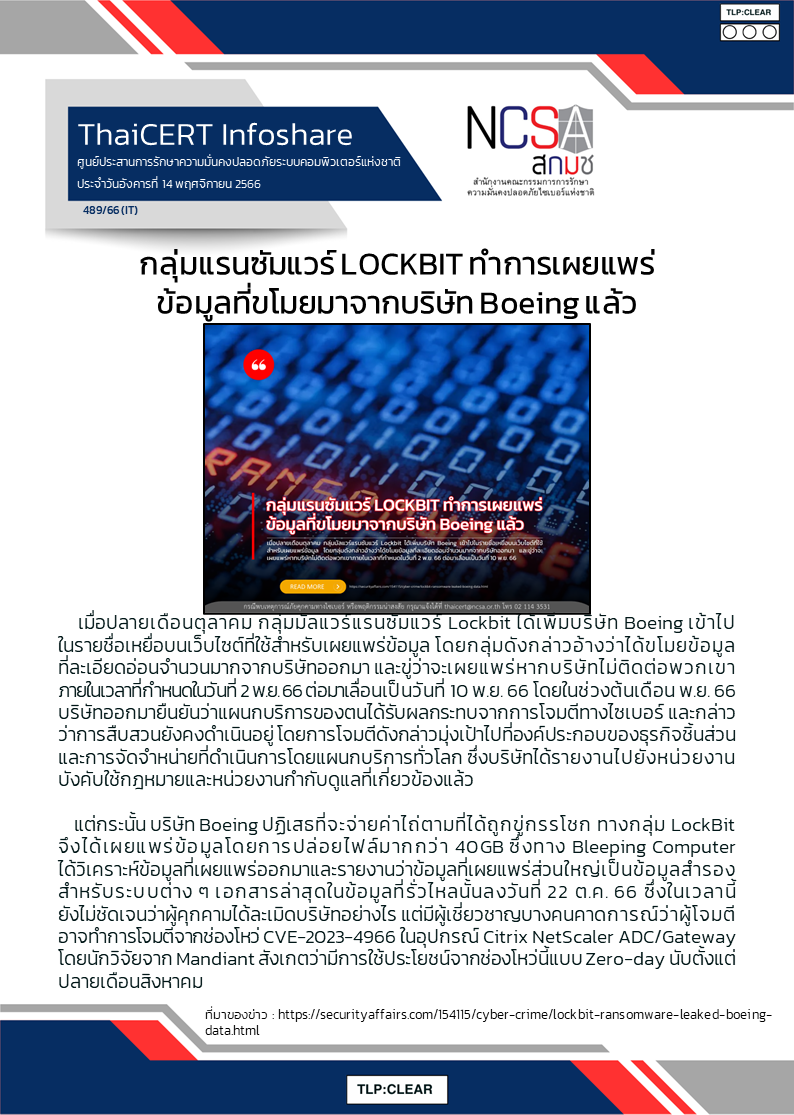
Honeywell: USB Malware Attacks On Industrial Orgs Becoming More Sophisticated
"Industrial giant Honeywell has published its sixth annual report on the threat posed by USB-borne malware to industrial organizations, warning of an increase in sophistication. The report is based on analysis conducted by the company’s Global Analysis, Research and Defense (GARD) team using data collected by a security product designed to detect and block malware on USB drives used in customers’ industrial environments."
https://www.securityweek.com/honeywell-usb-malware-attacks-on-industrial-orgs-becoming-more-sophisticated/
https://www.securityweek.com/wp-content/uploads/2024/04/2024_Honeywell_Gard_USB_Threat_Report_Research_Paper.pdf -
CISA Rolls Out New Guidelines To Mitigate AI Risks To US Critical Infrastructure
"The US government’s cybersecurity agency CISA has rolled out a series of guidelines aimed at beefing up the safety and security of critical infrastructure against AI-related threats. The newly released guidelines categorize AI risks into three significant types: the utilization of AI in attacks on infrastructure, targeted assaults on AI systems themselves, and failures within AI design and implementation that could jeopardize infrastructure operations."
https://www.securityweek.com/cisa-rolls-out-new-guidelines-to-mitigate-ai-risks-to-us-critical-infrastructure/
https://www.dhs.gov/sites/default/files/2024-04/24_0426_dhs_ai-ci-safety-security-guidelines-508c.pdf
New Tooling
- Prompt Fuzzer: Open-Source Tool For Strengthening GenAI Apps
"Prompt Fuzzer is an open-source tool that evaluates the security of your GenAI application’s system prompt against dynamic LLM-based threats."
https://www.helpnetsecurity.com/2024/04/29/prompt-fuzzer-open-source-genai-applications-security/
https://github.com/prompt-security/ps-fuzz
Vulnerabilities
-
R-Bitrary Code Execution: Vulnerability In R’s Deserialization
"HiddenLayer researchers have discovered a vulnerability, CVE-2024-27322, in the R programming language that allows for arbitrary code execution by deserializing untrusted data. This vulnerability can be exploited through the loading of RDS (R Data Serialization) files or R packages, which are often shared between developers and data scientists. An attacker can create malicious RDS files or R packages containing embedded arbitrary R code that executes on the victim’s target device upon interaction."
https://hiddenlayer.com/research/r-bitrary-code-execution/
https://thehackernews.com/2024/04/new-r-programming-vulnerability-exposes.html
https://www.darkreading.com/application-security/r-programming-language-exposes-orgs-to-supply-chain-risk -
Judge0 Sandbox Escape
"Judge0 is an open source service used to run arbitrary code inside a secure sandbox. The Judge0 website lists 23 clients using the service, with more than 300 self hosted instances available on the public internet and potentially many more within internal networks. Tanto Security disclosed vulnerabilities in Judge0 that allows an adversary with sufficient access to perform a sandbox escape and obtain root permissions on the host machine. These vulnerabilities were assigned CVE-2024-29021, CVE-2024-28185 and CVE-2024-28189."
https://tantosec.com/blog/judge0/
https://thehackernews.com/2024/04/sandbox-escape-vulnerabilities-in.html
https://www.infosecurity-magazine.com/news/judge0-sandbox-flaws-systems/
Malware
-
Muddling Meerkat Hackers Manipulate DNS Using China’s Great Firewall
"A new cluster of activity tracked as "Muddling Meerkat" is believed to be linked to a Chinese state-sponsored threat actor's manipulation of DNS to probe networks globally since October 2019, with a spike in activity observed in September 2023. A notable aspect of Muddling Meerkat's activity is the manipulation of MX (Mail Exchange) records by injecting fake responses through China's Great Firewall (GFW), an unusual and previously unseen behavior for the country's internet censorship system."
https://www.bleepingcomputer.com/news/security/muddling-meerkat-hackers-manipulate-dns-using-chinas-great-firewall/
https://insights.infoblox.com/resources-report/infoblox-report-muddling-meerkat-the-great-firewall-manipulator
https://thehackernews.com/2024/04/china-linked-muddling-meerkat-hijacks.html
https://www.darkreading.com/threat-intelligence/muddling-meerkat-poses-nation-state-dns-mystery -
Agent Tesla Campaign Targets US Education And Government Sectors
"Recent investigations have unveiled a coordinated attack that integrates two notorious malware types, Agent Tesla and Taskun. Each one is known for their disruptive capabilities, but their combined use marks a new level of sophistication. This analysis dissects the multifaceted approach used by adversaries, leveraging seemingly benign communication methods to deploy highly destructive payloads."
https://veriti.ai/blog/veriti-research/agent-tesla-campaign-targets-us-education-and-government-sectors/
https://www.hackread.com/agent-tesla-taskun-malware-us-education-govt/ -
The Darkgate Menace: Leveraging Autohotkey & Attempt To Evade Smartscreen
"McAfee Labs has recently uncovered a novel infection chain associated with DarkGate malware. This chain commences with an HTML-based entry point and progresses to exploit the AutoHotkey utility in its subsequent stages. DarkGate, a Remote Access Trojan (RAT) developed using Borland Delphi, has been marketed as a Malware-as-a-Service (MaaS) offering on a Russian-language cybercrime forum since at least 2018."
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/the-darkgate-menace-leveraging-autohotkey-attempt-to-evade-smartscreen/ -
Android Remote Access Trojan Equipped To Harvest Credentials
"The SonicWall Capture Labs threat research team has been regularly sharing information about malware targeting Android devices. We’ve encountered similar RAT samples before, but this one includes extra commands and phishing attacks designed to harvest credentials."
https://blog.sonicwall.com/en-us/2024/04/android-remote-access-trojan-equipped-to-harvest-credentials/ -
Ukrainian Military Intelligence Claims Attack On Website Of Russia’s Ruling Party
"Ukraine’s military intelligence agency, the GUR, launched a cyberattack against the online services of Russia's ruling United Russia party late last week, according to a source in the spy agency who spoke to several Ukrainian media outlets. The attack targeted United Russia’s servers, websites and domains, rendering the party’s digital platforms "partially inaccessible." The agency didn’t provide any further details about the operation."
https://therecord.media/ukraine-military-intelligence-untied-russia-party
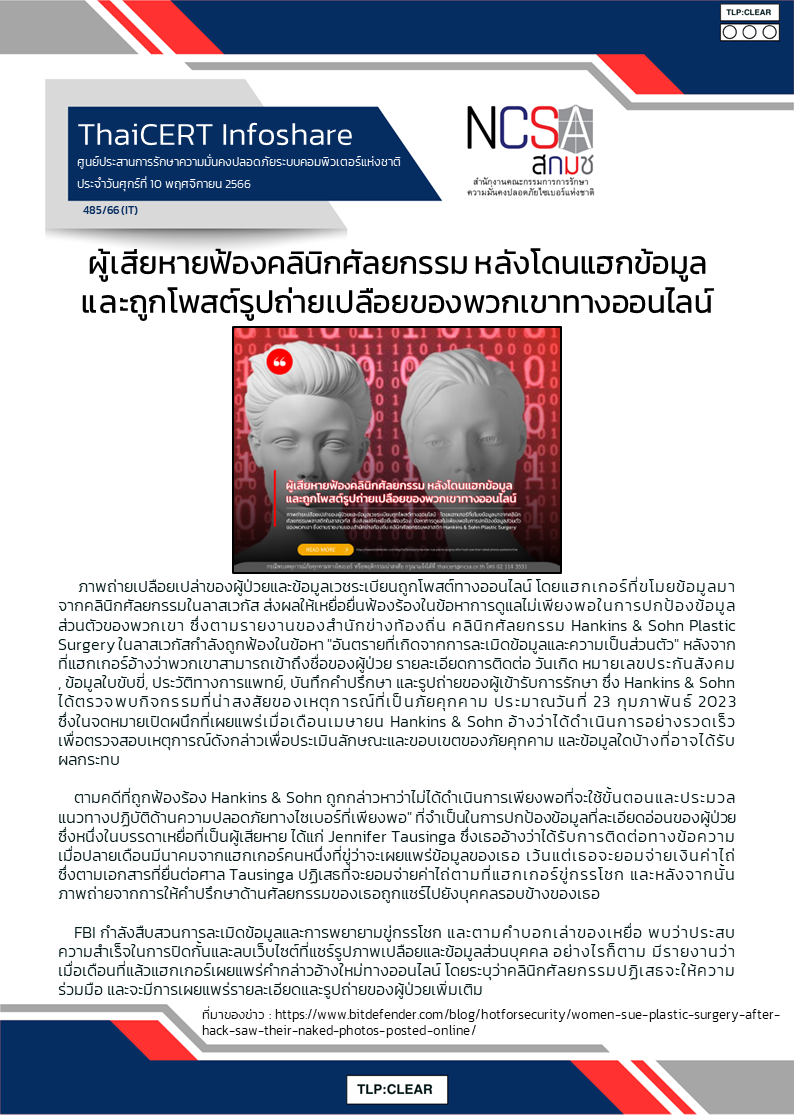
Breaches/Hacks/Leaks
-
London Drugs Pharmacy Chain Closes Stores After Cyberattack
"Canadian pharmacy chain London Drugs has closed all its retail stores to contain what it described as a "cybersecurity incident." The company has also hired external experts to investigate the cyberattack that impacted its systems over the weekend."
https://www.bleepingcomputer.com/news/security/london-drugs-pharmacy-chain-closes-stores-after-cyberattack/
https://www.theregister.com/2024/04/29/canada_london_drugs/ -
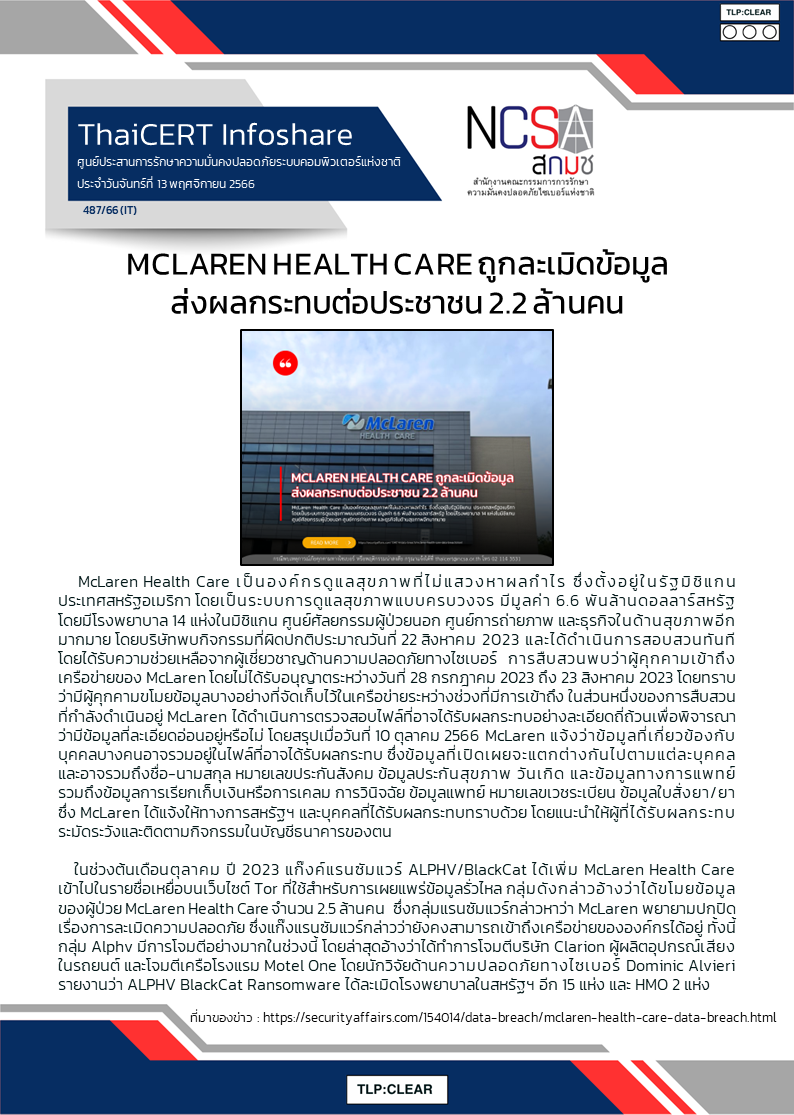
Collection Agency FBCS Warns Data Breach Impacts 1.9 Million People
"Financial Business and Consumer Solutions (FBCS) is warning 1,955,385 impacted individuals in the United States that the company suffered a data breach after discovering unauthorized access to specific systems in its network. FBCS is a nationally licensed debt collection agency in the U.S., specializing in collecting unpaid debts from consumer credit, healthcare, commercial, auto loans and leases, student loans, and utilities."
https://www.bleepingcomputer.com/news/security/collection-agency-fbcs-warns-data-breach-impacts-19-million-people/
https://www.securityweek.com/2-million-impacted-by-data-breach-at-debt-collector-fbcs/
https://securityaffairs.com/162514/cyber-crime/fbcs-data-breach.html -
Kansas City System Providing Roadside Weather, Traffic Info Taken Down By Cyberattack
"A Kansas City system providing real-time weather and traffic information to drivers along roads and highways was taken down by a cyberattack last week, damaging a critical tool during a weekend of dangerous storms. The Kansas City Scout System is run by the Departments of Transportation in Missouri and Kansas, calling itself the country’s only “bi-state traffic management center.” The National Weather Service in Kansas City supplies messages that are displayed on the signs along highways and on the organization's website or app."
https://therecord.media/kansas-city-traffic-system-cyberattack
General News
-
AI Is Creating a New Generation Of Cyberattacks
"Most businesses see offensive AI fast becoming a standard tool for cybercriminals, with 93% of security leaders expecting to face daily AI-driven attacks, according to Netacea."
https://www.helpnetsecurity.com/2024/04/29/offensive-ai-cyberattacks/ -
Closing The Cybersecurity Skills Gap With Upskilling Programs
"The list of skills technologists and organizations need to succeed grows with each new tech advancement, according to Pluralsight. But for many organizations, budgets and staff continue to shrink."
https://www.helpnetsecurity.com/2024/04/29/tech-skills-gap/ -
Standard Chartered CEO On Why Cybersecurity Has Become a 'disproportionately Huge Topic' At Board Meetings
"As the chief executive of one of the largest banks in the world, Bill Winters is constantly identifying, evaluating and taking steps to mitigate risks. And over the last decade at London-based Standard Chartered, cybersecurity has become a major focus of his in terms of investment, employee training and board discussions. "That just reflects the magnitude of the threat," according to Winters."
https://therecord.media/standard-chartered-ceo-bill-winters-cybersecurity-culture-board-focus -
How We Fought Bad Apps And Bad Actors In 2023
"A safe and trusted Google Play experience is our top priority. We leverage our SAFE (see below) principles to provide the framework to create that experience for both users and developers. Here's what these principles mean in practice:"
https://security.googleblog.com/2024/04/how-we-fought-bad-apps-and-bad-actors-in-2023.html
https://www.bleepingcomputer.com/news/security/google-rejected-228-million-risky-android-apps-from-play-store-in-2023/
https://thehackernews.com/2024/04/google-prevented-228-million-malicious.html
https://www.securityweek.com/google-says-it-blocked-2-28-million-apps-from-google-play-store/
https://securityaffairs.com/162528/mobile-2/google-play-malicious-app-2023.html
https://www.theregister.com/2024/04/29/google_rejected_apps/ -
Machines Vs Minds: The Power Of Human Ingenuity Against Cyber Threats
"Most people remember the iconic movie Terminator, in which the cyborg T-800 was dispatched back in time from the year 2029 with the mission to eliminate Sarah Connor. She was destined to give birth to the future leader of the human resistance against machines, thus threatening their dominance. If Sarah were killed, humanity's fate would be sealed, and the earth would succumb to the rule of machines."
https://www.tripwire.com/state-of-security/machines-vs-minds-power-human-ingenuity-against-cyber-threats -
Addressing Risk Caused By Innovation
"By embracing a proactive approach to cyber-risk management, companies can better detect, prevent, and mitigate cyber threats while integrating the latest state-of-the-art technology."
https://www.darkreading.com/cyber-risk/addressing-risk-caused-by-innovation -
Should Cybersecurity Leadership Finally Be Professionalized?
"Professionalization could be a solution to the increased cybersecurity risk for corporate and national security; and the mental health and even physical liberty of CISOs. But it’s not easy."
https://www.securityweek.com/should-cybersecurity-leadership-finally-be-professionalized/
อ้างอิง
Electronic Transactions Development Agency(ETDA) 






 สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand

 สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
 สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand

 สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
 สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand
