-
UAT-9244 Targets South American Telecommunication Providers With Three New Malware Implants
"AT-9244 used dynamic-link library (DLL) side-loading to activate multiple stages of their infection chain. The actor executed “wsprint[.]exe”, a benign executable that loaded the malicious DLL-based loader “BugSplatRc64[.]dll”. The DLL reads a data file named “WSPrint[.]dll” from disk, decrypts its contents, and executes them in memory to activate TernDoor, the final payload. TernDoor is a variant of CrowDoor, a backdoor deployed in recent intrusions linked to China-nexus APTs such as FamousSparrow and Earth Estries. CrowDoor is a variant of SparrowDoor, another backdoor attributed to FamousSparrow. CrowDoor has also been observed in previous Tropic Trooper intrusions, indicating a close operational relationship with FamousSparrow."
https://blog.talosintelligence.com/uat-9244/
https://www.bleepingcomputer.com/news/security/chinese-state-hackers-target-telcos-with-new-malware-toolkit/
-
ClipXDaemon: Autonomous X11 Clipboard Hijacker Delivered Via Bincrypter-Based Loader
"In early February 2026, Cyble Research & Intelligence Labs (CRIL) identified a new Linux malware strain delivered through a loader structure previously associated with ShadowHS activity. While ShadowHS samples deployed post-exploitation tooling, the newly observed payload is operationally different. We have named it ClipXDaemon, an autonomous cryptocurrency clipboard hijacker targeting Linux X11 environments."
https://cyble.com/blog/clipxdaemon-autonomous-x11-clipboard-hijacker/
-
New BoryptGrab Stealer Targets Windows Users Via Deceptive GitHub Pages
"We recently found the existence of a new stealer binary that collects browser and cryptocurrency wallet data, system information, and common files, among others. We designated this new stealer BoryptGrab. Certain variants of the stealer can download a PyInstaller backdoor, which we refer to as TunnesshClient. TunnesshClient establishes a reverse Secure Shell (SSH) tunnel to enable comunication with the attacker."
https://www.trendmicro.com/en_us/research/26/c/boryptgrab-stealer-targets-users-via-deceptive-github-pages.html
-
Bing AI Promoted Fake OpenClaw GitHub Repo Pushing Info-Stealing Malware
"Fake OpenClaw installers hosted in GitHub repositories and promoted by Microsoft Bing’s AI-enhanced search feature instructed users to run commands that deployed information stealers and proxy malware. OpenClaw is an open-source AI agent that gained popularity as a personal assistant capable of executing tasks. It has access to local files and can integrate with email, messaging apps, and online services. Due to its widespread local access, threat actors saw an opportunity to collect sensitive information by publishing malicious skills (instruction files) on the tool's official registry and GitHub."
https://www.bleepingcomputer.com/news/security/bing-ai-promoted-fake-openclaw-github-repo-pushing-info-stealing-malware/
-
Wikipedia Hit By Self-Propagating JavaScript Worm That Vandalized Pages
"The Wikimedia Foundation suffered a security incident today after a self-propagating JavaScript worm began vandalizing pages and modifying user scripts across multiple wikis. Editors first reported the incident on Wikipedia's Village Pump (technical), where users noticed a large number of automated edits adding hidden scripts and vandalism to random pages. Wikimedia engineers temporarily restricted editing across projects while they investigated the attack and began reverting changes."
https://www.bleepingcomputer.com/news/security/wikipedia-hit-by-self-propagating-javascript-worm-that-vandalized-pages/
-
APT36: A Nightmare Of Vibeware
"Pakistan-based threat actor APT36, also known as Transparent Tribe, has pivoted from off-the-shelf malware to "vibeware", an AI-driven development model that produces a high-volume, mediocre mass of implants. Using niche languages like Nim, Zig, and Crystal, the actor seeks to evade standard detection engines while leveraging trusted cloud services, including Slack, Discord, Supabase, and Google Sheets, for command and control."
https://businessinsights.bitdefender.com/apt36-nightmare-vibeware
https://www.darkreading.com/cyberattacks-data-breaches/nation-state-actor-ai-malware-assembly-line
https://www.bankinfosecurity.com/nation-state-hackers-play-vibes-a-30920
https://hackread.com/pakistan-apt36-indian-govt-networks-ai-vibeware/
-
Seedworm: Iranian APT On Networks Of U.S. Bank, Airport, Software Company
"The Iranian APT group Seedworm (aka MuddyWater, Temp Zagros, Static Kitten) has been active on the networks of multiple U.S. companies since the beginning of February 2026, with activity continuing in recent days following U.S. and Israeli military strikes on Iran that have sparked conflict in the region. A U.S. bank, software company and airport, and non-governmental organizations in both the U.S. and Canada, have experienced suspicious activity on their networks in recent days and weeks. The software company is a supplier to the defense and aerospace industries among others, and has a presence in Israel, with the company’s Israel operation seeming to be the target in this activity."
https://www.security.com/threat-intelligence/iran-cyber-threat-activity-us
https://www.theregister.com/2026/03/05/mudywater_backdoor_us_networks/
-
FBI Targeted With ‘suspicious’ Activity On Its Networks
"The FBI found evidence that its networks had been targeted in a suspected cybersecurity incident, the bureau confirmed on Thursday, without sharing any further details. “The FBI identified and addressed suspicious activities on FBI networks, and we have leveraged all technical capabilities to respond,” the agency said in a statement. “We have nothing additional to provide.”"
https://cyberscoop.com/fbi-targeted-with-suspicious-activity-on-its-networks/
-
LIMINAL PANDA: China’s Emerging Espionage Threat In The Semiconductor And Technology Sectors
"LIMINAL PANDA, a suspected China-nexus cyber-espionage actor, has recently emerged as an active player in the global threat landscape. The group began operating around 2020 and has focused its intelligence collection on a range of high-value targets in East Asia, Southeast Asia, and Western nations engaged in research and development of advanced technologies, including semiconductors, defense technologies, and telecommunications. While not a well-known actor (yet) like APT41 or Mustang Panda, LIMINAL PANDA shows an accelerating trajectory of evolution in capabilities, experimenting with the convergence of more traditional phishing criminal enterprises with sophisticated cloud exploitation and supply chain compromise."
https://brandefense.io/blog/liminal-panda-apt-group/
-
Breaches/Hacks/Leaks
-
New Jersey County Says Malware Attack Took Down Phone Lines, IT Systems
"One of the largest counties in New Jersey is dealing with a cyberattack that disrupted the phone lines and IT systems used across government offices. Passaic County, home to nearly 600,000 people in Northern New Jersey, published a statement on Wednesday evening warning residents that it is aware of a “malware attack” affecting county IT systems and phone lines. “Our team is actively working with federal and state officials to investigate and contain the issue,” the county said."
https://therecord.media/new-jersey-county-says-malware-attack-took-down-phones
 ️ ThaiCERT ได้ติดตามสถานการณ์ภัยคุกคามทางไซเบอร์ และพบประกาศด้านความมั่นคงปลอดภัยจาก WatchGuard เกี่ยวกับช่องโหว่ CVE-2026-3342 ซึ่งเป็นช่องโหว่ประเภท Out-of-bounds Write ใน WatchGuard Fireware OS โดยอาจเปิดโอกาสให้ ผู้โจมตีที่ยืนยันตัวตนแล้วและมีสิทธิ์ผู้ดูแลระดับ privileged administrator สามารถใช้ management interface ที่เปิดเข้าถึงได้ เพื่อ รันโค้ดด้วยสิทธิ์ root บนอุปกรณ์ที่ได้รับผลกระทบ ส่งผลให้มีความเสี่ยงสูงต่อการถูกยึดระบบหรือแก้ไขการตั้งค่าความมั่นคงปลอดภัยของอุปกรณ์.
️ ThaiCERT ได้ติดตามสถานการณ์ภัยคุกคามทางไซเบอร์ และพบประกาศด้านความมั่นคงปลอดภัยจาก WatchGuard เกี่ยวกับช่องโหว่ CVE-2026-3342 ซึ่งเป็นช่องโหว่ประเภท Out-of-bounds Write ใน WatchGuard Fireware OS โดยอาจเปิดโอกาสให้ ผู้โจมตีที่ยืนยันตัวตนแล้วและมีสิทธิ์ผู้ดูแลระดับ privileged administrator สามารถใช้ management interface ที่เปิดเข้าถึงได้ เพื่อ รันโค้ดด้วยสิทธิ์ root บนอุปกรณ์ที่ได้รับผลกระทบ ส่งผลให้มีความเสี่ยงสูงต่อการถูกยึดระบบหรือแก้ไขการตั้งค่าความมั่นคงปลอดภัยของอุปกรณ์.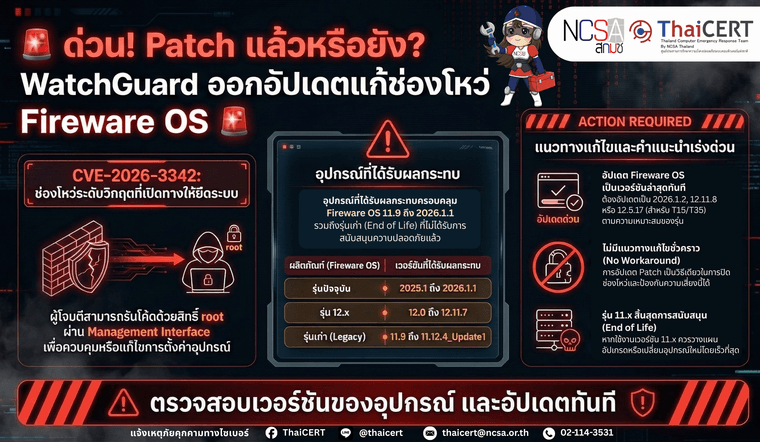








 แหล่งอ้างอิง:
แหล่งอ้างอิง: