
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand 


สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand 
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand  !
!
Healthcare Sector
Telecom Sector
Government/Law/Policy
Vulnerabilities
Malware
Breaches/Hacks/Leaks
General News
อ้างอิง
Electronic Transactions Development Agency(ETDA) 
Healthcare Sector
Industrial Sector
New Tooling
Vulnerabilities
Malware
Breaches/Hacks/Leaks
General News
 (CIS Controls
(CIS Controls ) is an iterative update to version 8.0. It offers prescriptive, prioritized, and simplified cybersecurity best practices that provide a clear path for you to improve your organization’s cyber defense program."
) is an iterative update to version 8.0. It offers prescriptive, prioritized, and simplified cybersecurity best practices that provide a clear path for you to improve your organization’s cyber defense program."อ้างอิง
Electronic Transactions Development Agency(ETDA) 
Energy Sector
Healthcare Sector
Industrial Sector
New Tooling
Vulnerabilities
Malware
Breaches/Hacks/Leaks
General News
อ้างอิง
Electronic Transactions Development Agency(ETDA) 

สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand 
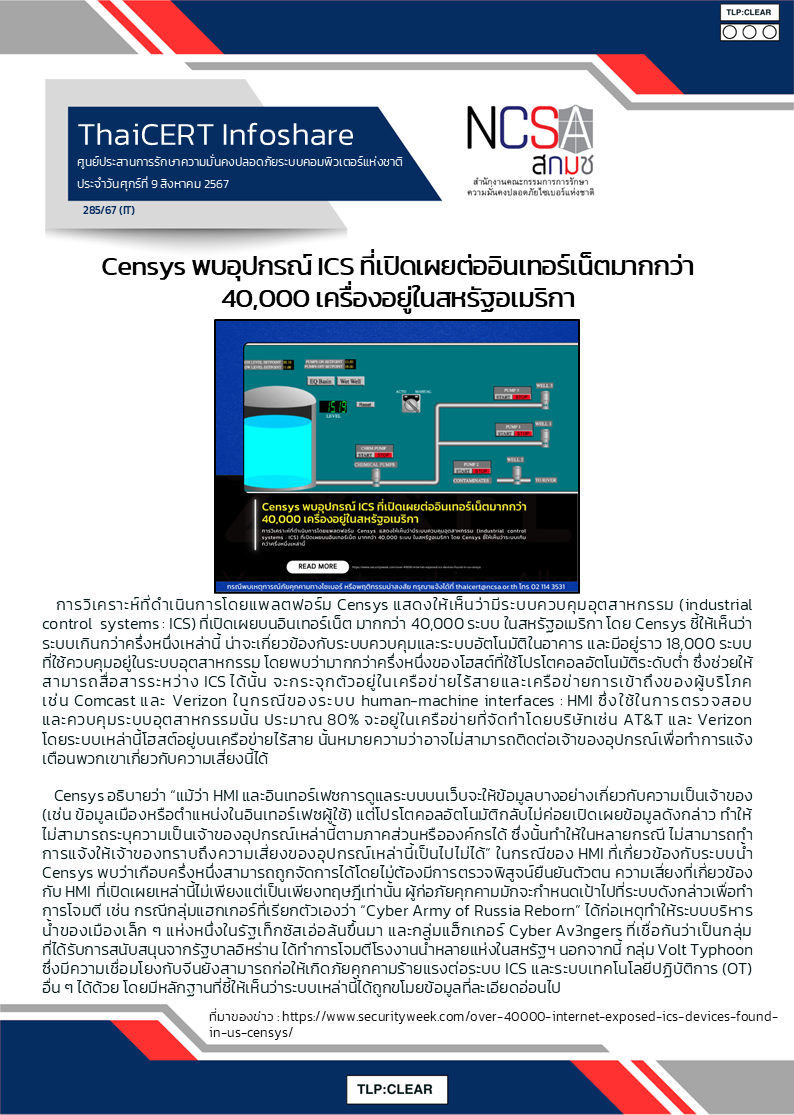
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand 
Cyber Security Agency of Singapore (CSA)ได้เผยแพร่เกี่ยวกับความยืดหยุ่นของข้อมูลกลายเป็นสิ่งสำคัญมากขึ้นในโลกดิจิทัล ช่วยให้มั่นใจได้ว่าข้อมูลของคุณยังคงเป็นความลับ รักษาความสมบูรณ์ (กล่าวคือ ไม่มีการแก้ไขโดยไม่ได้รับอนุญาต)
และพร้อมใช้งานเมื่อคุณต้องการเข้าถึง
เป็นเรื่องสำคัญที่บุคคลและองค์กรต่างๆ ต้องใช้มาตรการเชิงรุกเพื่อปกป้องข้อมูลของตนจากภัยคุกคามทางไซเบอร์ที่อาจเกิดขึ้น
แนะนำให้บุคคลและองค์กรดำเนินการดังต่อไปนี้:
สามารถสำรองข้อมูลได้ในสื่อหลายประเภท รวมถึง (แต่ไม่จำกัดเพียง):
• สื่อบันทึกข้อมูลแบบถอดได้
• ไดรฟ์ฮาร์ดดิสก์ภายใน
• การจัดเก็บข้อมูลบนคลาวด์
• สื่อสิ่งพิมพ์
การพึ่งพาการสำรองข้อมูลเพียงสื่อเดียวอาจทำให้ข้อมูลไม่มีความยืดหยุ่นเพียงพอ ดังนั้น บุคคลและองค์กรจึงควรพิจารณาใช้ตัวเลือกการสำรองข้อมูลแยกกันอย่างน้อยสองตัวเลือกสำหรับข้อมูลสำคัญบนสื่อที่แตกต่างกันเพื่อให้แน่ใจว่าข้อมูลมีความทนทาน นอกจากนี้ เพื่อรักษาความสมบูรณ์ของข้อมูล บุคคลและองค์กรควรดำเนินการทดสอบการสำรองข้อมูลเป็นประจำเพื่อยืนยันว่าไม่มีข้อผิดพลาดใดๆ เพื่อให้แน่ใจว่าขั้นตอนการกู้คืนข้อมูลมีความน่าเชื่อถือและมีประสิทธิภาพในการป้องกันการสูญเสียข้อมูลที่อาจเกิดขึ้น
ใช้การเข้ารหัสข้อมูล
การเข้ารหัสข้อมูลเป็นสิ่งสำคัญเพื่อให้แน่ใจว่าข้อมูลที่ละเอียดอ่อนจะเป็นความลับและปลอดภัย ข้อมูลสำคัญทั้งหมด ไม่ว่าจะอยู่ในที่จัดเก็บหรือระหว่างการส่ง ควรเข้ารหัสโดยใช้ขั้นตอนการเข้ารหัสที่แข็งแกร่งเพื่อให้แน่ใจว่าข้อมูลจะไม่สามารถอ่านได้แม้ว่าจะถูกขโมย (ผ่านการบุกรุกอุปกรณ์) หรือถูกดักจับ (ผ่านการโจมตีแบบ Man-in-the-Middle) บุคคลสามารถพิจารณาใช้เครื่องมือเข้ารหัสที่มีชื่อเสียงและ/หรือคุณลักษณะการเข้ารหัสในตัวเพื่อปกป้องข้อมูลของตนจากการเข้าถึงโดยไม่ได้รับอนุญาต องค์กรควรใช้การเข้ารหัสมาตรฐานอุตสาหกรรม (เช่น AES-256) เพื่อให้แน่ใจว่าข้อมูลจะเป็นความลับและปกป้องข้อมูลที่ละเอียดอ่อน
อัปเดตซอฟต์แวร์และระบบเป็นประจำ
ตรวจสอบให้แน่ใจว่าซอฟต์แวร์และระบบทั้งหมดติดตั้งแพตช์ความปลอดภัยล่าสุดเพื่อแก้ไขช่องโหว่ใหม่ๆ เพื่อลดความเสี่ยงของการเสียหายของข้อมูลหรือการขโมยข้อมูล บุคคลและองค์กรควรพิจารณาเปิดใช้คุณสมบัติการแพตช์ความปลอดภัยอัตโนมัติเพื่อให้แน่ใจว่ามีการแพตช์ตามเวลาและสม่ำเสมอ
คอยติดตามข้อมูลเกี่ยวกับภัยคุกคามทางไซเบอร์ที่เกิดขึ้นใหม่
เมื่อภัยคุกคามทางไซเบอร์มีการพัฒนาอย่างต่อเนื่อง สิ่งสำคัญคือทั้งบุคคลและองค์กรต่าง ๆ จะต้องรับทราบข้อมูลเกี่ยวกับภัยคุกคามทางไซเบอร์ล่าสุดและแนวทางปฏิบัติที่ดีที่สุดสำหรับการรักษาความปลอดภัยทางไซเบอร์
นอกจากนี้ องค์กรต่างๆ ควรปฎิบัติดังนี้
การดำเนินการแบ่งส่วนเครือข่าย
การดำเนินการนี้มีวัตถุประสงค์เพื่อแยกส่วนต่างๆ ของเครือข่ายขององค์กรออกจากกัน เพื่อจำกัดการบุกรุกที่อาจเกิดขึ้นกับส่วนเครือข่ายเดียว และลดความเสี่ยงของการละเมิดข้อมูลโดยรวมให้เหลือน้อยที่สุด การแบ่งส่วนเครือข่ายจะสร้างบันทึกการรับส่งข้อมูลบนเครือข่ายที่สามารถตรวจสอบกิจกรรมออนไลน์ที่เป็นอันตรายได้เป็นประจำ ข้อมูลที่เป็นความลับอย่างยิ่งควรอยู่ในส่วนเครือข่ายที่ไม่มีการเข้าถึงอินเทอร์เน็ตโดยตรง
บังคับใช้การควบคุมการเข้าถึงที่เข้มงวด
ควรดำเนินการนี้ร่วมกับมาตรการตรวจสอบสิทธิ์ที่เข้มงวดเพื่อลดความเสี่ยงในการเข้าถึงข้อมูลสำคัญโดยไม่ได้รับอนุญาต โดยการยึดตามหลักการของสิทธิ์ขั้นต่ำที่ให้สิทธิ์การเข้าถึงที่จำเป็นเพียงเล็กน้อยแก่พนักงานแต่ละคน ความเสี่ยงจากภัยคุกคามจากภายในและการเข้าถึงโดยไม่ได้รับอนุญาตสามารถลดลงได้อย่างมาก นอกจากนี้ องค์กรต่างๆ ยังได้รับการสนับสนุนให้ตรวจสอบรายการควบคุมการเข้าถึงเป็นประจำและลบบัญชีที่ไม่ได้ใช้งานใดๆ
จัดทำแผนการกู้คืนจากภัยพิบัติ
ควรพัฒนาแผนการกู้คืนเพื่อให้องค์กรมีแนวทางที่เป็นระบบในการตอบสนองต่อการหยุดชะงักและฟื้นฟูการดำเนินธุรกิจอย่างมีประสิทธิภาพ องค์กรควรพิจารณาสิ่งต่อไปนี้ในแผนการกู้คืนจากภัยพิบัติ:
• ข้อมูลที่สำคัญจะถูกจำแนกและแบ่งส่วนอย่างไร
• ควรสำรองข้อมูลอย่างไร
• ข้อมูลจะถูกกู้คืนได้อย่างไร
• ความถี่ในการสำรองข้อมูล
องค์กรต่างๆ ยังได้รับการสนับสนุนให้ตรวจสอบแผนการตอบสนองเป็นประจำเพื่อให้แน่ใจว่าแผนเหล่านั้นได้รับการอัปเดตและมีประสิทธิผล
ดำเนินการฝึกอบรมด้านความปลอดภัยไซเบอร์
องค์กรต่างๆ สามารถพิจารณาให้ความรู้แก่พนักงานเกี่ยวกับภัยคุกคามทางไซเบอร์ทั่วไปและแนวทางปฏิบัติที่ดีที่สุดด้านความปลอดภัยทางไซเบอร์ การฝึกอบรมอาจครอบคลุมถึงการสร้างความตระหนักรู้เกี่ยวกับความสำคัญของความปลอดภัยของข้อมูล เทคนิคฟิชชิ่งล่าสุด และแนวทางปฏิบัติที่ดีที่สุดสำหรับการรักษาความปลอดภัยของข้อมูล การให้ความรู้และทักษะด้านความปลอดภัยทางไซเบอร์แก่พนักงานจะช่วยลดโอกาสที่พนักงานจะตกเป็นเหยื่อของเหตุการณ์ทางไซเบอร์ได้ จึงช่วยลดความเสี่ยงในการสูญเสียข้อมูลลงได้
ด้วยการใช้มาตรการป้องกันที่แข็งแกร่งและการเฝ้าระวังภัยคุกคามทางไซเบอร์ที่เปลี่ยนแปลงไป บุคคลและองค์กรจะสามารถเตรียมพร้อมในการเพิ่มความยืดหยุ่นของข้อมูลได้ดีขึ้น
อ้างอิง
https://www.csa.gov.sg/alerts-advisories/Advisories/2024/ad-2024-015
สามารถติดตามข่าวสารได้ที่ webboard หรือ Facebook NCSA Thailand 